Cybersecurity professionals are consistently under assault from all angles. The common perception is that these angles are all the unique threats they face in the wild each day, the proliferation of easy-to-use tools by threat actors, insider threats, an expansion of the attack surface they need coverage for as digital innovation continues to push companies forward, and the growing number of tools they need to respond to from an alerting perspective. But in addition to all these things, the most daunting of these challenges to tackle for security professionals is neither technological or security-related in nature but the numerous operational challenges they face within their business, which mainly boil down to: not enough money, not enough people and not enough time. Add to this growing concerns of a recessions, reports of tech layoffs, and tightening budgets, these operational problems' ugly heads begin to display in a much more prominent way. The question then becomes for security professionals, how do we ensure we can continue to meet our security and compliance outcomes while we are constantly operating from a position that is bombarded by constraints.
Well first, it is a good thing to recognize that sometimes constraints can actually support and cause innovation to flourish, rather than be a hindrance to it. This is true because under the right mindset constraints can be a motivating challenge and cause a level of narrowed focus that leads to efficient solution sets. When there are no constraints, complacency sets in and individuals take the path of least resistance to solving a problem. However, when you have a limiting constraint, your mind is forced to look for partnerships, other pieces of data, or connective elements from other projects that often lead to new and innovative products and business processes. For example, when a manager limits budget for a project, a person may look to innovative open source solutions that provide the same level of outcomes as a paid solution they're using or they may look to consolidate a number of feature sets from other tools into a singular solution. When a manager faces a resource constraint, they may look to different technology sets that is able multiply the outcomes of a person's work or streamline it so they can do more with their current employee set. Finally, when a manager limits time for a project, the team may find innovative ways to increase the efficiency of their work, thus bringing in the project and hitting the shortened deadline.
This post will explore common constraints security professionals face and how security vendors can do more to help security operators tackle their day to day operational problems head on, while still achieving the security and compliance outcomes one would expect from adopting top tier security software solutions. It will examine what you can be doing to demand more of your software vendors in regards to supporting you as you tackle these operational constraints. We will investigate how good security vendor relationships can not only help you achieve a positive return on investment (ROI) on your security tooling investments but can unlock innovation for you in a constraint-based economy and role within organizations.
Operational Challenge #1: Budgeting
We often hear from security professionals that they do not have enough budget to accomplish everything they need to from a security perspective. Their ability to invest in the necessary software tooling to address the growing complexity of cloud infrastructure, the people to make sense of the data from that tooling, and the procedural operations to respond to the alerts from that tooling is constantly being evaluated from a ROI perspective by the executive leadership of the business. Security leaders are constantly defending themselves as a cost-center within the business and not as a critical part of a company's revenue-generating operations. CSO online has a great quote about why CISOs are viewed as a cost-center within the business when they write, "“Many business leaders are now keen to participate in cyber transformation, but they find the wide use of security jargon and vain metrics deeply frustrating. It leaves them unclear about key threats targeting their businesses, the strength of their existing defenses, or what investment is required. They feel like they are pouring money in a leaky bucket because cybersecurity teams struggle to translate the value of their initiatives into the language of the business: money,” says Phil Zongo, CEO of the Cyber Leadership Institute, a training organization, and a member of the Emerging Trends Working Group at the professional association ISACA."
There are a few things that security leaders can do to combat this perception within the business; even though, it is important to acknowledge that you will most likely not be able to escape this perception in its entirety. First, is to acknowledge that this is how you are viewed within the business and think about how you message and position your security investments and outcomes to leadership. On the investment side, you can demonstrate that you are not just asking for budget for tooling for toolings sake but that you are mindful of ensuring that you can get maximum coverage out of each and everyone of your security tools. We are starting to see this within the market as company's demand that their security tooling for the cloud is comprehensive across the infrastructure, application stack, and user base; this is why security tools have begun packing their cloud workload protection platforms (CWPP) with cloud native application protection (CNAP), cloud security posture management (CSPM), and cloud access security broker (CASB) feature sets to address cloud-native, infrastructure, and SaaS security all along with their core workload protection features for the cloud. Showing that your tools can get you this type of comprehensive coverage is a great first step to demonstrating that you can control costs within the business by consolidating toolsets. I will caution here that there will never be a tool that meets every security need or use case but you can focus on consolidating comprehensive coverage in the areas most important to your business.
While this shows you control costs, these costs are still seen as non-revenue producing or non-impactful to core business operations and KPIs. Security professionals can change this viewpoint of executive leadership teams through a combination of quantitative calculations of security's impact and through better messaging and positioning. I had a friend who worked at a large streaming provider. He said that his security leadership team would consistently go report to the board metrics around number of attacks blocked, SOC response time metrics, and a number of other jargon-laced metrics that meant nothing to the leadership of the business. It sounded cool but they had no way to translate that into either bottom or top line value for the business. My friend said that the moment they went into the board and changed the conversation to a dashboard about business impact, i.e. how much a vulnerability risk in the business would cost the business if it was exploited and the likelihood of those exploits occurring, then the boards ears perked up and they began having serious conversations about where and how to invest in cybersecurity solutions for the business.
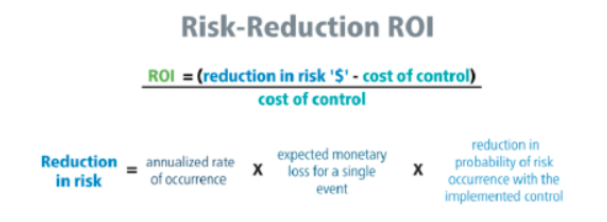
This dashboard better helped quantify for executives the impact of security on the business. But there was qualitative messaging and positioning that helped with this too. They began to use messaging that utilized security as a competitive differentiator for the business, positioning the streaming provider as the leader in the space due to its ability to maintain secure and private PII and IP from customers and their content providers. They also began messaging in terms of the business not just quantitatively but qualitatively as well. They referenced risk in relation to internal business units and specific application sets. They were then able to paint scenarios backed by quantitative risk data of what would happen operationally to the business, not just financially if a vulnerability was to be exploited. For example, in terms of a ransomware scenario, employees would be locked out of their workstations and hence their ability to login to critical company actions to provide support for end customers, security response in the case of SOC professionals being locked out, or marketing access to their communication platforms to issue guidance to the business. These types of qualitative scenarios helped paint the picture for the business as to why reducing security risk in critical areas was such an important effort.
Operational Challenge #2: Resourcing
Security leaders are constantly under threat from a second operational challenge and that is the inability for them to higher enough subject matter expert resources in order to staff the roles they need to keep the business secure and compliant. “Nearly every security team has been, is, or will be struggling with finding and retaining talent. Indeed, 45% of security respondents said their department is currently experiencing a shortage of employees.” This Forbes article on continued cybersecurity staffing challenges, highlights the very real impact this has on a businesses ability to secure the business as businesses often struggle with having the same vulnerabilities in their environment for 5+ years without the ability to resolve the risk due to the constant in and out nature of talent in that industry.
There are a number of things that security leaders can do within their business to better tackle the constraints of resourcing without having to resort to demanding more budget to higher more open recs that they struggle to fill. That same Forbes articled cited, 30% growth in job openings and 600,000 unfilled positions in the US alone. First, security leaders can do more to ensure that security as a practice does not engage in gate-keeping when it comes to breaking into the industry. There are plenty of diverse and smart talent pools out there that face barriers of entry when companies use unrealistic year of experience or certification requirements for entry-level positions, lack on the job training opportunities, and/or don't have tooling that complements the skillsets that a businesses' employees do have.
Secondly, security leaders can help shift security culture and do more to make security everyone's responsibility as opposed to the responsibility of a few individuals within the organization. The very notion that security can only be achieved by a select few subject matter experts is flawed and leads us to ignore the users or employee sets that can be the most common denominator attack/risk vector into your business. This can occur through a combination of security awareness training, intuitive tooling that fits security into their workflow, or enforces security policy in a helpful but non-intrusive way. Lastly, security leaders can help relieve the security resourcing burden by using tooling that helps automate away time-consuming, mundane tasks and helps prioritize risk across the business. This combination of technology and doing more in our own efforts to democratize security to more functions within the business can be a powerful innovation functions for businesses dealing with resourcing constraints.
Demand more of Security Vendors: your Partners in a Secure Future
Companies should ensure that their security vendors are able to help them tackle the operational issue of budget in the following ways:
- Offer flexible business/purchasing models - today's era demands consumption, fixed pricing, hourly/monthly/yearly billing, etc depending on the needs of your business. Your vendors should be flexible in their models to help you financially obtain the software in the way that makes the most sense for your needs.
- Consolidate tooling along use cases - this is the example I gave above about cloud use cases and the consolidation of CWPP, CSPM, and CNAP tooling.
- Access to data for your quantitative analysis - demand open access to the data within the platforms you utilize. Stable, predictable, and transparent API access to data is critical in calculating the ROI of security tooling.
- Clear and impactful reporting - reports and their visualizations should help tell the qualitative stories above and paint the picture of impact to critical applications and data sets.
Deepfence has focused on each of these cases as it has built out its Deepfence Cloud solution. Deepfence is on a mission to continue to innovate in how it brings its innovative security tech to market and the feature sets it includes. This HelpNet Security article outlines how the Deepfence Cloud solution democratizes the ability for ANY company to simplify how they gain visibility into and secure their cloud native applications and infrastructure.
We are able to offer flexible billing and security models that scale based on the workloads that need protection as well as flat site licenses for companies that just want an all you can eat price for securing their environment regardless of scale or growth throughout the year. As outlined in the article above, Deepfence is able to provide comprehensive coverage of your cloud infrastructure and applications through a combination of CWPP, CNAP, and CSPM feature sets. Everything within the Deepfence platform is built using an API-first development methodology and so our APIs and access to your security data is a first class citizen within our technology development efforts and this translates into reporting as we utilize our own system to secure our own organizational risk. But beyond the use cases above, Deepfence is on a mission to democratize critical security tooling by making it open source and focusing on providing value where commoditized software cannot. You can read more about this mission in my post on Deepfence here.
Companies should equally demand that their security vendors help them tackle the operational issue of resourcing in the following ways:
- Help democratize security functions across the business - this will ensure that more people within the business are able to perform security functions as part of their day to day operations to keep the company safe. A subset of this point is bringing security closer to the functions your company does have skillsets for - i.e development and making it easier to implement security utilizing those frameworks.
- Automate routine, time-consuming tasks - this will allow the security professionals a company does have to focus their efforts on more strategic, higher order of operations activity that is more likely to impact the bottom line of the business.
- Prioritize risk - this ensures that the resources you do have are able to focus their limited time and energy on the most impactful security risks to your business, helping limit monetary or operational impact if one of those risks were to be exploited.
Deepfence is on a mission to focus on the human elements of security through software, while still delivering on the promise of cutting edge security innovation and detection mechanisms from a technical standpoint. Deepfence's tooling fits well within common DevSecOps practices and workflows so you can easily integrate it and manage it using cloud, infrastructure, and development teams already at your disposal. We help your business continue to shift-left in your development practices while securing your business on the right side and properly!
Deepfence's platform also helps companies better utilize the resources they do have by prioritizing risk for them within the environment. We do this by not only showing companies what their attack surface looks like (i.e. where their vulnerabilities lie) but the attack paths to that surface (i.e. where and how threat actors can actually access those vulnerabilities). This better helps companies decide where to prioritize their response efforts and where to write better security policy to prevent threat actors from utilizing certain TTPs (tactics, techniques and procedures) within your organization's environment to exploit risk.
Whether you utilize Deepfence to help solve both your security and operational challenges within your business or rely on another combination of processes and tools, it is imperative that you demand your tooling solve both technical and operational risk within your security program. Share with me your stories below of the operational burdens and challenges you face as a modern security professional. What best practices have you found useful in confronting these challenges? In what ways has your relationship with your security vendor helped or hindered your ability to solve these operational issues? Leave your comments below and share this post so we can better help democratize security solutions to organizations everywhere!






Comments